Registry Plus™ Maximizing Data Security in Web Plus
For basic information, read Security Features in Web Plus or download Web Plus Security Features and Recommendations. [PDF-224KB] Information about data security is also available.
Web Plus is a form-authenticated, ASP.NET application that is hosted on Internet Information Services (IIS) running on Microsoft® Windows® 2000 or later server operating systems. In a typical setting, the Web server sits in the Demilitarized Zone (DMZ) between the external and internal firewalls; SQL Server, where the Web Plus database is stored, resides inside the internal firewall as part of the trusted network.
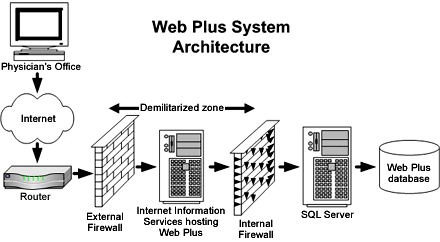
The security of Web Plus depends mostly on the security of the client computer, the communication channel between the client and the Web server, the Web server, the base operating system, and the configurations of the firewalls on either side of the Web server. It is very important that the hosting agency have a security policy in place and document the users (and their assigned roles) who will have access to the Web Plus application and the database. The hosting agency will be responsible for encrypting the Web Plus database if required. Security breaches by social engineering attacks are always a consideration; special attention is required in all parts of the system to prevent such attacks. Use of strong passwords for logging in to Web Plus is highly recommended, and sharing of user accounts should be prohibited.
Security Features of the Operating Infrastructure
Security on the Client Computer
The client computer should be protected from any kind of Trojan horse or spyware attacks by installing anti-virus and anti-spyware software, and ensuring that these programs are up-to-date.
Secure Communication Channel and Server Certificate
Web Plus relies on the existence of a Secure Socket Layer (SSL) channel between the Web server and client browser for the protection of data exchanged over the Internet. To set up an SSL channel, a server certificate must be installed on the Web server and SSL encryption must be enabled on the Web site containing the application. The server certificate can be created in-house if a certificate server is available, or purchased from a third-party commercial organization called a certificate authority. A certificate of 128-bit cyber strength is the industry standard for secure communication over the Internet and is highly recommended.
Implementing Two-Factor Authentication Using Client Certificates
Form-based authentication may be supplemented with a two-factor authentication scheme in which clients are authenticated based on “what they know” and “what they have”—
- The “what they know” part of the scheme is fulfilled by the login page of Web Plus, as users must provide their user ID and password to access the system.
- The “what they have” part can be implemented by configuring IIS to require clients to have certificates to connect to the Web Plus site. When Web Plus is configured this way, the hosting agency is responsible for creating client certificates and distributing them to users. These certificates are installed on the computers on which users connect to the Web Plus site. These client certificates provide stronger authentication by ensuring only authorized computers can access Web Plus.
Hardening the Web Server and Operating System
Windows 2003 Server with IIS6 is highly recommended because of enhanced security over Windows 2000 server. Follow the guidelines from Microsoft to harden the Web server and the base operating system. The IIS Lockdown tool available from Microsoft’s download site can be used to automate several security steps to reduce the vulnerability of the Windows 2000 Web server. Microsoft recommends that you—
- Apply the latest patches to the operating system and IIS. Use the Microsoft Baseline Security Analyzer to detect patches and updates that may be missing from the current installation.
- Do not install IIS as part of the operating system installation. Rather, install it later, after you have updated and patched the base operating system. Then install IIS, apply patches, and harden the IIS configuration.
- When installing IIS, do not install File Transfer Protocol (FTP Server), Microsoft Front Page 2000 Server Extensions, Internet Service Manager (HTML), NNTP Service, or Visual InterDev RAD Remote Deployment Support. However, install SMTP to support e-mail in Web Plus.
- Disable unnecessary protocols including NetBIOS and Server Message Block (SMB) on the Internet-facing Network Interface Card (NIC) and remove Web Distributed Authoring and Versioning (WebDAV).
- Delete or disable unused accounts. Rename the administrator account, disable the guest and Internet User (IUSR) accounts, and create a custom anonymous Web account with the fewest privileges. If you run IIS Lockdown, add your custom user to the Web Anonymous Users group that is created. IIS Lockdown does not allow the Web Anonymous Users group to access to system utilities or write to Web content directories.
- Use strong access controls to protect sensitive files and directories. Set access at the directory level whenever possible. Enforce strong password policies, restrict remote logons, and disable null sessions.
- Ensure that only the .NET Framework Redistributable package is installed on the server and no Software Development Kit (SDK) utilities are installed. Do not install Visual Studio.NET on production servers. Debugging tools should not be available on the Web server. Ensure that access to powerful system tools and utilities, such as those contained in the \Program Files directory, is restricted. Remove all sample files.
- Relocate Web roots and virtual directories to a non-system partition to protect against directory traversal attacks.
Secure Connection to the Database
If SQL server authentication is used, the user ID and password are embedded in the connection string, but the connection string is stored in encrypted form in web.config using Windows Data Protection Application Programming Interface (DPAPI). If Windows authentication is used, the user’s credentials are not included in the connection string, but the connection string still is encrypted to hide the database server’s IP address, port number, and other information.
Windows authentication is preferred from a security point of view because it does not transmit the user’s credentials over the network. Windows authentication requires a mirrored ASP.NET process account to be created as a local Windows account with the same name and password on the database server. ASP.NET is a least-privileged account created while installing .NET framework on the Web server. By default, all ASP.NET applications run under the security context of this account. After creating the account in Windows, create a SQL Server login for the account and grant it access to Web Plus database.
It is recommended that the SQL Server listen on a port number different from the default port, 1433. This port should be opened in the internal firewall to allow the Web server to access the database.
Configuring ASP.NET for Security
Various security options can be configured in the web.config and machine.config files. The settings depend on local security requirements and administrative preferences. In most cases, leaving the settings at the default values should provide the required security.
- Page last reviewed: January 8, 2015
- Page last updated: January 13, 2015
- Content source:
- Maintained By:


 ShareCompartir
ShareCompartir